Passwords remain the main form of user authentication despite the inconvenient trade-off between security and usability. Since passwords are firmly rooted in many areas of information security, future usage is expected, and better care needs to be taken to support the security without usability degradation.
Regular users prefer using simple, easy-to-remember passwords to using secrets with better security guarantees. Even the simplest password-retrieving attacks, like brute-force or dictionary attacks, are effective when targeted on this group of users [34]. Creating and remembering passwords capable of withstanding these attacks requires an additional effort, and letting this responsibility to users yields secure passwords only rarely [35].
Two different aspects can primarily affect the security of passwords: password entropy and password storage.
Password entropy
Generally, password entropy can influence its unpredictability in terms of attacker’s ability to guess the password by brute force (exhaustive search). Password entropy is defined only vaguely [36], and many online meters exist, evaluating the security of a given password inconsistently [37]. The entropy is measured in bits, given by a function of its length and the size of the character set. Having a set of c distinct characters used to build a password of length n, the final entropy can be calculated by
![]()
However, this calculation does not correspond with the real-life password entropy. Since many sources with leaked user passwords can be easily found online and indepence between various characters cannot be taken for granted, the actual entropy of any leaked password is lower. Even if sufficient in length or chosen from an extensive character set, a password containing common password patterns will be guessed by a dictionary attack successfully in significantly less time than by brute-forcing. Therefore, suitable password quality meters should also account for existing password databases and common password patterns. An example of a realistic password entropy estimator is zxcvbn [38], providing better security guarantees than common password policies.
According to NIST [39], a memorized secret shall be at least eight characters long. However, passwords should be longer to achieve resilience against guessing attacks. Oesh et al. [40] generated 147 million passwords using numerous password generators and analyzed the vulnerability of passwords to these attacks. They estimated a minimum length of 10 and 18 characters to be resilient against online and offline attacks, respectively.
Even though the average password length seems to be rising over the years [41], recent research by NordPass shows that the most commonly used passwords are still the weakest ones [42]. According to the study by Shen et al. [41], only 3.29% out of more than 6 million analyzed passwords contained special characters, implying that most users choose characters from alphanumeric sets only and thus choose passwords of small entropy.
Password storage
There are only two general solutions to storing passwords – either they are remembered by the user or written down in some form.
The first approach becomes strongly unusable with the approximate average number of user accounts being 25 [43], and potentially even higher [44]. Secure passwords are difficult to remember, and users tend to reuse them or use weaker ones to avoid the cognitive burden [45, 46]. By using the same password for different accounts, even a secure one, when leaked from an insecure provider, all other accounts get compromised. The work by Das et al. [47] shows that 43% of the observed user accounts reused the same passwords directly, and the other 19% contained identical substrings.
The second solution is, therefore, more suitable. The ideal practice is to store a set of passwords encrypted in digital form to protect them from theft and make them securely accessible from any location.
Secure password
Since a concrete definition is non-existent, a secure password in the scope of this work either has
- a length resilient to brute-force attacks – at least ten characters,
- a sufficient character set – alphanumeric with at least one special symbol,
- composition resilient to dictionary attacks – no common password patterns, preferably randomly built by a CSPRNG
or is in form of a passphrase, which
- is a sequence of unrelated, preferably random words – at least three,
- has at least 18 characters.
Both variants must not contain personal information directly linkable to the user’s identity or information in public knowledge, like birth dates or names of family members.
Password manager
Password manager is a software designed to solve the security issues of password entropy and password storage, increasing both the security and usability of password management. A typical password manager stores all user entries encrypted and provides means for effective import, retrieval and adjustment of entries. The entries consist of passwords and other associated information stored in a local database or cloud. The storage location is commonly referred to as a vault.
The vault should be secured by a standardized encryption cipher with the primary key derived from the user password by key strengthening, and proper setting of all critical parameters. A single primary password addresses the password reuse problem – the user needs to remember nothing but the primary password to access any entry in the vault.
From the usability point of view, features of a password manager should include:
- copying passwords and other information into clipboard,
- customizable auto-type – a keyboard shortcut to fill different types of login forms automatically,
- a generator of secure passwords,
- a browser extension for auto-fill of credentials in login forms,
- means for vault synchronization across devices.
Security issues
With usability-enhancing features several security weaknesses arise . Copying information to clipboard is the essential functionality provided by most password managers. Nevertheless, there is a possibility that the information ends up in the wrong places – either gets stolen from the clipboard by malware or inserted into an insecure location by the user accidentally. A suitable password manager should clear the clipboard automatically after some time or action.
Auto-fill is another praised feature accelerating the workflow by automatically filling the credentials of website accounts. Here the security of password managers can fail due to an insecure implementation of target websites. Websites can be vulnerable to attacks such as XSS attacks, allowing stealing credentials before being sent to the server, or clickjacking by auto-fill in website iframes, tricking the user into taking action causing auto-fill without their consent.
Oesh et al. [40] examined the auto-fill security of numerous password managers and showed that most of them were vulnerable to some auto-fill attacks. They suggest that the most effective available remediation of these vulnerabilities is disabling auto-fill without user intervention.
Password database backup
A securely accessible copy of the password database is crucial to preserve the safety of using a password manager, especially if sensitive information, like bank account credentials, is stored. Any form of database backup comes with risk that needs to be evaluated by each user individually according to their skills and storage options. Generally, the backup should be protected by different means than the primary password if it gets forgotten or compromised. Recommended approaches are:
- paper backup – the password vault in plaintext stored in a safe location[1], or
- digital backup – the password vault encrypted, e. g. on a hard drive[2].
Storing the backup database on the cloud is not recommended since physical possession grants more safety assurances. However, a database duplicate stored on the cloud is better than no backup at all – if the original database was cloud-based, a different cloud provider is needed for the backup file.
Another approach is remembering one more secure password on top of the database primary password. This additional password would be then used to access a fallback account, typically an e-mail client. Most websites provide fallback authentication by verifying the e-mail address in case of a forgotten password, so access to some accounts could be assured even if the password vault is not accessible.
Candidates
The set of selected and tested candidates consists of Bitwarden, KeePassXC, Password Safe, pass, Mozilla Firefox and Google Chrome password managers. Other options were early evaluated as inappropriate for the group of users defined in the scope of this work.
This section describes only suitable password managers, with an overview of their features in Table Comparison of password management features. Further results are described in the appendices, with a summarized overview in Table Overview.
KeePassXC
KeePassXC is a multi-platform local-based password manager released under the GPLv2 and GPLv3 licenses. It is an actively developed fork of KeePassX[3], providing additional features and bug fixes. KeePassX was created to bring KeePass, a Windows-based password manager, to Linux systems and eventually also to macOS or BSD systems. All password managers in the KeePass family use file databases in KDBX format, which is commonly accepted to be imported by many other password managers.
Import of entries is possible from several KeePass format versions. Older versions like KDB or KDBXv2 are upgraded automatically. The vault can be exported to CSV, and HTML for paper backups.
KeePassXC features a brilliant password generator. The default length of the generated password is 20 characters, chosen from a sufficient character set. Passphrases can be generated as well, consisting of seven words by default. The password entropy is displayed in bits and evaluated by the zxcvbn tool.
Other features include a customizable vault hierarchy, customizable auto-type, searching for entries or database health reports[4].
KeePassXC is designed well in terms of usable security. Most of the defaults are secure, including clearing clipboard after 10 seconds or asking for consent to perform auto-type. The user is warned sufficiently about actions potentially rendering the vault insecure, like exporting to plaintext formats or enabling automatic auto-fill of credentials within the browser extension. However, there is no effective password policy during creating a new database: the user is not warned even if a single-character primary password is chosen. Also, the locking of the database is not automated by default.
Browser integration is available for Mozilla Firefox, Microsoft Edge, four different Google browsers, and the Tor-Browser. The extension is secure and considerably configurable, but its usability is not acceptable for beginner users. The desktop application needs to launch together with the browser every time for the entry retrieval to work. The application needs to be paired manually with the extension. If something goes wrong, e. g., the desktop application is not running, the response is completely unclear for both beginner and intermediate users, as shown in Figure 2.
The default encryption mode of AES is not mentioned in the documentation. According to KeePassXC source code [49], the vault is encrypted using AES-CBC. The primary password is strengthened using the memory-hard Argon2d PBKDF.
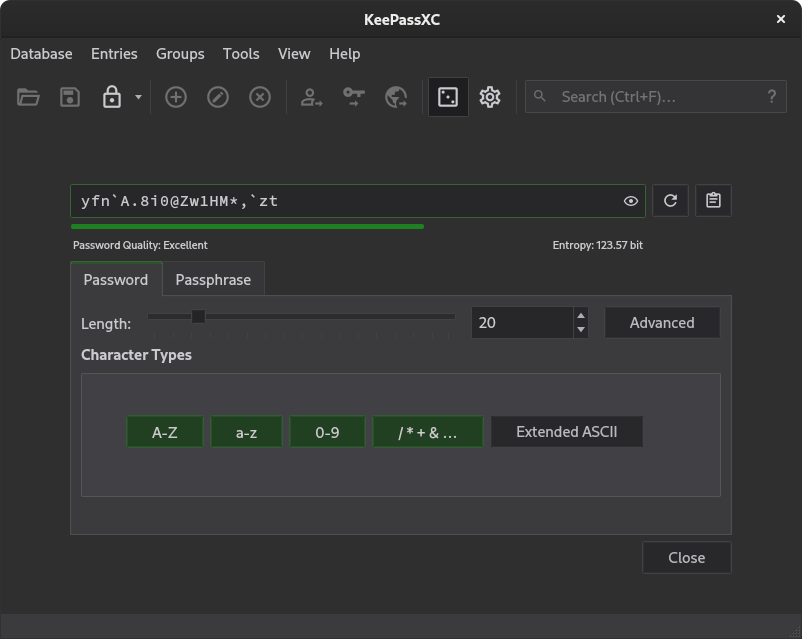
Figure 1: Features of KeePassXC password generator.
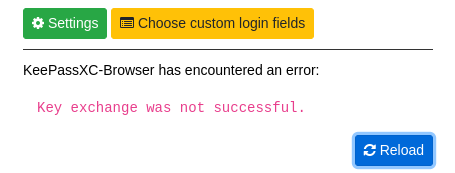
Figure 2: KeePassXC browser extension error dialog.
Bitwarden
Bitwarden is a multi-platform cloud-based password manager licensed under the GPLv3 license. Some parts of Bitwarden’s functionality need a premium account.
By default, Bitwarden encrypts all data on the client-side and stores it in the Microsoft Azure Cloud in the US. However, users are not forced to trust the security of the cloud provider. Bitwarden can be deployed on their own servers[5].
The vault is stored in JSON format. Bitwarden allows import from various database formats[6] and export to JSON or CSV, including an encrypted export.
This password manager differs from other solutions by exceptional usability. Apart from a modern visual appearance, the content is tailored to be easily understandable by beginner users while preserving a considerable amount of settings for intermediate users. It is also the only password manager providing the option to set a primary password hint. Nevertheless, some default settings should be changed to increase security.
One of the strongest qualities of Bitwarden is the automatic cross-platform synchronization, which removes the burden of synchronizing the password vault manually. The application is supported on all major operating systems and can be integrated into eight different internet browsers. Furthermore, it comes as a web and mobile application, yielding very flexible vault access.
Another powerful feature is the Bitwarden browser extension. The extension contains all essential functions of the desktop or web version and can be used independently. The extension features a directly customizable password generation and many settings, including the configurable URL matching policy. User intervention is always needed to perform auto-fill.
The Bitwarden password generator produces 14-character passwords from an alphanumeric character set without special symbols by default. The policy can be customized, and users should include special characters or increase the length to generate secure passwords.
An alarming default setting is the clearing of clipboard – it is not performed by default and should be turned on by the user.
The vault is encrypted using AES-256-CBC. The only supported PBKDF is PBKDF2, with 100,001 iterations on the client-side and additional 100,000 iterations on the servers. The client-side iteration count can be configured in the web application.
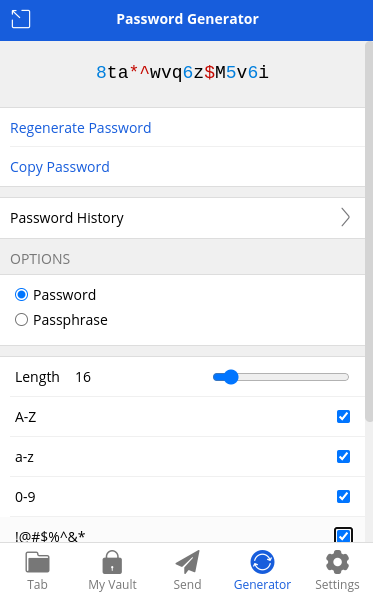
Figure 3: Features of Bitwarden browser extension password generator.
Mozilla Firefox
Mozilla Firefox is an open-source internet browser released under the Mozilla Firefox License 2.0.
The overall security of Mozilla Firefox with study of security-enhancing Firefox plugins is one of the research topics of CyberSec4Europe. The complete evaluation was conducted by a separate team, supervised by Václav Matyáš.
Firefox features an integrated password manager implemented using the Network Security Services (NSS) open-source library. The storage and transport of passwords by NSS tool pk12util conforms with PKCS#12 – the RSA standard for personal information exchange syntax. PKCS#12 describes the format of archive files containing personal identity information like private keys or certificates.
Unlike other browser-based password managers, Firefox allows locking the vault with a primary password, providing an additional layer of security. The primary password plays the role of a primary password in password management. It is not possible to enter the Firefox vault and use stored login information during the session without knowing the primary key.
The vault is stored encrypted on the user system in a folder dedicated to user profile information, separated from the Firefox program, in the key4.db SQLite file. A Firefox account needs to be created to allow synchronization across different devices with the Firefox browser. Access to profile data on the synchronization server is not guaranteed – Firefox recommends backing up the profile files manually [50]. The Firefox vault can be exported into a CSV file.
The default encryption cipher is AES-CBC with a 256-bit encryption key, and PBKDF2 is used to derive a primary key from the primary password [51]. The user cannot change encryption options. Password generation is available during registrations, creating a 15-character password and automatically adding a new login entry to the vault if allowed. Passwords cannot be generated on demand otherwise. Auto-fill can be disallowed for the whole vault as well as for specific entries only.
pass
pass is a command-line password management tool licensed under the GPLv2 license. The encryption is implemented using the GNU Privacy Guard (GPG), an implementation of the OpenPGP standard defined in RFC 4880 [52]. GPG is licensed under the GPL License and included in most major Linux distributions.
Simplicity is the main principle of this password manager. The tool stores all entries in one folder, each in a GPG-encrypted file. The hierarchy of the vault is thus designed by the user completely. Additional features include secure password generation based on /dev/urandom, yielding 25-character passwords, and automatic clear of clipboard, which is set to 45 seconds by default. It is, however, important to specify the -c option while password generation to avoid printing the password on the standard output and copy it to clipboard instead.
Extensions can enhance the functionality – importing entries from other password managers, supporting one-time-password tokens, easier updating of passwords and others.
Password management recommendations
Bitwarden was selected as an optimal password manager for both beginner and intermediate users. Taking care of a local database file might be unsafe for beginners – a cloud-based password manager is a safer option for preventing accidental deletion of the vault. This password manager is most likely to keep long-term users thanks to its intuitive GUI, well-designed browser extension and automatic cross-device synchronization. The study by Fagan et al. [53] shows that most of the actual users of password managers keep using them because of usability benefits, and some do not care about security. After changing some default settings, Bitwarden will deliver the desired usability with appropriate security included.
KeePassXC is recommended for intermediate users with higher security demands. This password manager provides the greatest amount of features and settings. In contrast with Bitwarden, KeePassXC provides a stronger password generator and PBKDF for primary key derivation, and all of its functionality is free. Both Bitwarden and KeePassXC provide a CLI intermediate users can use to automate simple tasks.
Some password management is better than none. A browser-based solution is also a noteworthy option if a user is not motivated enough to use a desktop password manager with all its features. These password managers are enabled in browsers by default and do not need installation. Mozilla Firefox password manager with primary password protection enabled is selected as a suitable solution. Compared to Google Chrome, the entries are guaranteed to be encrypted on any system thanks to NSS, and auto-fill can be adjusted for individual entries.
Lastly, intermediate users looking for simplicity can use pass to store entries locally in a fully flexible vault architecture secured by GPG.
Comparison of password management features
| Bitwarden | KeePassXC | pass | Mozilla Firefox | |
| primary password | yes | yes | yes | configurable |
| fallback authentication | via hint | no | no | no* |
| secure password generator** | configurable | yes | yes | no*** |
| vault synchronization | yes | manual | manual | with Firefox account |
| Windows support | yes | via KeePass | no | yes |
| macOS support | yes | yes | yes | yes |
| mobile application | yes | no | no | yes |
| browser extension | yes | yes | no | native |
| automatic clipboard clearing | configurable | yes | yes | yes |
| autofill | yes | yes | no | yes |
| default encryption cipher | AES-CBC | AES-CBC | AES-CFB | AES-CBC |
| PBKDF | PBKDF2 | Argon2d | platform dependent |
PBKDF2 |
* Primary password reset deletes all entries in the vault [54].
** Secure passwords are described at the beginning of this section.
*** There is a request to include special characters into the Firefox password generator opened for three years [55].
Overview
| license | latest version as of May, 2022 | default encryption | default PBKDF | supported platforms | |
| Bitwarden | GPLv3 clients + GPLv2 server | V1.58.0 Apr 26, 2022 |
AES-CBC | PBKDF2 | Linux, Windows, macOS |
| KeePassXC | GPLv2 + GPLv3 | V2.7.1 Apr 6, 2022 |
AES-CBC | Argon2d | Linux, Windows, macOS |
| Password Safe | Artistic License 2.0 | V3.58.0 Dec 20, 2021 |
Twofish | ? | Linux, Windows |
| pass | GPLv2 | V1.7.4 Jun 11, 2021 |
AES-CTF | platform-dependent | Linux, macOS |
| Mozilla Firefox | Mozilla Firefox License 2.0 | V100.0 May 3, 2022 |
AES-CBC | PBKDF2 | Linux, Windows, macOS |
| Google Chrome | BSD + other | V101.0.4951.67 May 12, 2022 |
platform-dependent | platform-dependent | Linux, Windows, macOS |
Appendices
Password Safe
Password Safe is a multi-platform local-based password manager released under the Artistic License version 2.0. The Linux support was until recently in just a beta version [11], but now it is considered to be stable. However, the official pages state that the Windows version provides additional features.
The manager uses its own Password Safe database format. The vault is encrypted by 256-bit Twofish, which cannot be changed. The documentation does not mention the method and iterations of the primary key derivation.
Passwords can be imported from KDBX formats and XML. The vault can be exported to the Password Safe or XML formats only. The user is warned about the security issues during the XML export, and confirmation by the primary key is needed.
A strong feature of Password Safe is automatic backups of the vault. The default number of backups is three files, and a backup is created every time the database changes. Unfortunately, the default location for backup is the folder where the database is located, but the location can be changed manually in the settings, as well as the number of backup files being stored.
No fallback authentication is offered as a design option to minimize the attack surface. Other features include automatic clearing of clipboard, automatic locking of database or auto-type – each configurable by the user.
Apart from using a non-standardized encryption algorithm, a potential weakness of this password manager is the GUI. There are alternatives to this password manager with comparable security qualities, whose GUI is significantly better in terms of usability and visual appearance. Since most users put usability first, Password Safe is not an ideal option for long-term use in its current state. Additionally, some settings are very unintuitive, e. g. the managing of password policies or settings of keyboard shortcuts without any further explanations.
Passwords Safe also does not provide a browser extension.
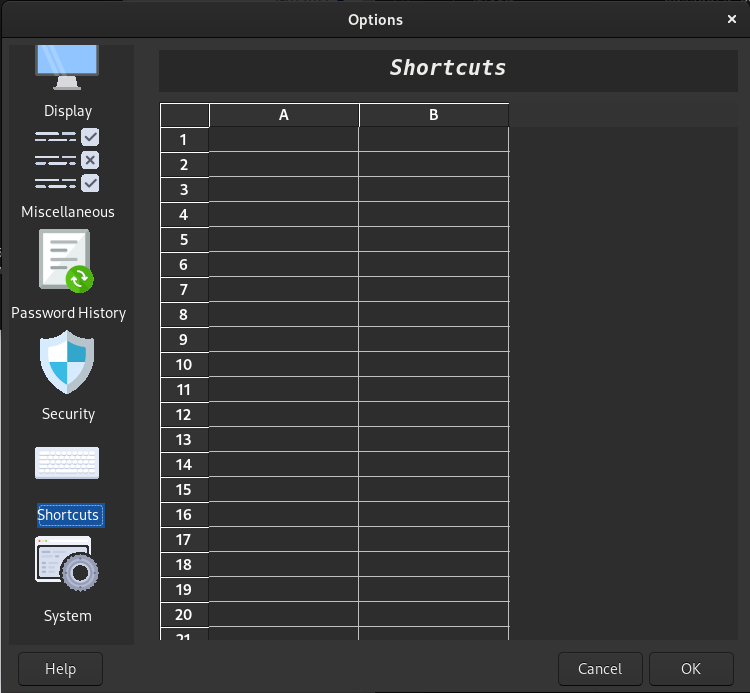
Figure 4: Password Safe keyboard shortcuts settings.
Figure 5: Password Safe vault.
Google Chrome
The Google Chrome browser is based on the open-source Google Chromium. The Google-authored part of Chromium is released under the BSD license, and other parts are subject to a number of other licenses [81]. An integrated password manager is provided and enabled by default.
Similarly to Firefox, the password vault is stored encrypted in an SQLite file on the system, and a Google account is needed to synchronize the vault across devices[11].
Encryption is dependent on the operating system hosting the browser. On Linux systems, Chromium chooses the type of vault storage according to the desktop environment. Daemon-based system keyring implementations – GNOME keyring or KWallet – are used if available. By default, Chromium detects the keyring automatically, but the use of a specific keyring can be configured manually. If no compatible keyring is detected, Chrome will store the passwords on the system in plaintext [83, 84].
GNOME Keyring and KWallet are solutions for storing cryptographic keys and passwords in GNOME and KDE desktop environments, respectively. By default, the vault is integrated with the user login and automatically unlocked at the beginning of each desktop session. The primary password to the vault is then the user system password. If automatic login or a different keyring password is set on the system, the keyring will ask for the user password each time the Chrome session begins. Otherwise, the vault is unavailable. After the end of the session, the vault stays unlocked and needs to be locked manually. As stated in the GNOME keyring daemon documentation, it does not conform with the PKCS#12 standard.
The vault can be exported into a CSV file. Automatic sign-in is enabled by default and needs to be turned off to involve user interaction. The feature can be either turned on or off for the whole vault, and it cannot be specified for individual entries. The password generation is similar to Firefox again: a password can be generated during a new registration on a website, yielding a 15-character password saved automatically. There is no other way of generating new passwords.
- More reasoning can be found at https://keepassxc.org/blog/2020-10-03-paper-backup. ↑
- See section Data-at-rest encryption. ↑
- The development of KeePassX officially stopped on Dec 9., 2021 [48]. ↑
- Numerous additional features are available and the exhaustive list can be found at https://keepassxc.org/project. ↑
- The Bitwarden Help center provides a detailed tutorial on self-configured domains for Linux, macOS and Windows servers. ↑
- The exhaustive list of supported formats for import is available at https://bitwarden.com/help/import-faqs/#q-what-file-formats-does-bitwarden-support-for-import. ↑
- Primary password reset deletes all entries in the vault [54]. ↑
- Secure passwords are defined in Section Secure password. ↑
- There is a request to include special characters into the Firefox password generator opened for three years [55]. ↑
- This information was not found in the documentation. ↑
- Password synchronization was removed from Chromium on March 15, 2021, and continues to be available in the proprietary Chrome browser only [82]. ↑
