27 June 2022
CyberSec4Europe – Open Tool Portal

The recently published Open Tool Portal presents two groups of open tools that are of interest to both security experts and users with little or medium experience in security tools and technologies.
Open tools for professional use
This portal section presents five expert tools developed within the project, described briefly in the sections that follow. The main tool is the Cyber Sandbox Creator (CSC) – an open-source tool for building lightweight virtual laboratories for cybersecurity education, testing and certification. Since February 2020, CSC has been used in practice numerous times and has been continuously improved to address the needs of a broad range of users. We identified six target user roles that can benefit from the tool: educator, trainee, researcher, developer, specialist, and auditor. CSC is referenced in a CyberSec4Europe deliverable (Virtual lab for open-source tools education and research), and was also accompanied in another deliverable (Common virtual lab with open-source tools for research and development), where it was integrated with parts of the expert tools described in the following sections. To create a virtual lab environment, a knowledgeable user first writes a sandbox definition: semi-structured text files describing virtual machine parameters and configuration of network topology. Then, CSC uses these files as input to generate an intermediate definition for Vagrant and Ansible. Finally, the result is distributed to regular users, who execute CSC to instantiate the actual virtual lab.
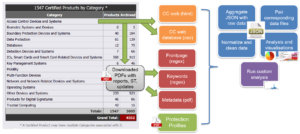
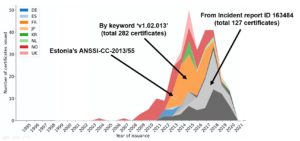
The sec-certs set of tools downloads, processes, and analyses security certificates issued under Common Criteria and NIST FIPS 140-2 schemes and turn these into computer-searchable and analysable datasets. As a result, the following and other questions can be answered:
- What chips are impacted by flaw found in certified library X? Which certificates are relevant for my certified product Z? What products are affected by specific CVE vulnerability?
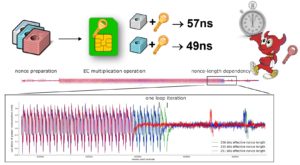
- What devices were analysed for timing side-channel leakage? Is ECC 521-bit curves supported?
- What are the trends of whole certification ecosystem regarding the archival rate, achieved security levels, usage of protection profiles and others?
The certification reports are the most detailed publicly available documents, yet currently available as pdf report in non-standardised format with only some metadata extracted (e.g., FIPS140-2 extracts referenced certificates). The sec-certs downloads source documents (PDF describing certified configuration and security target, CSV and HTML with additional metadata) and extract relevant information using regular expressions created for specific areas like certificate references, cryptographic algorithms, security assurance levels and many others. The information extracted is stored in open format (JSON) and further used to analyse certificates, map them to other sources like CVE vulnerability database and construct aggregate visual presentation available at https://seccerts.org. The sec-certs tools also allow to process all data locally including additional own, non-public documents.
SCRUTINY is then a set of tools allowing to verify that all devices (e.g., cryptographic smartcards) are matching the expected forensic profile to detect chips of different revision, malfunctioning, or even counterfeited one.
RTT toolset provides easy to use assessment of the randomness properties of data generated by truly random data generator (e.g., physical TRNG) or pseudo-random generator (e.g., AES ciphertext, PRNG).
The fifth set of tools is provided for exhaustive implementation testing of existing RSA and ECC implementations and verify that the required security-relevant checks like known invalid inputs tested (EC point not on curve, invalid curve parameters…) are performed. Automatic analysis of library output artefacts (generated keys, side-channel leakage…) is collected and any deviances (even if not directly exploitable) from the common behaviour are searched for detected. A black-box analysis is performed, allowing for analysis also on the closed, proprietary devices. The typical use-case scenarios are:
- Automatic testing during development (e.g., continuous integration).
- Initial thorough analysis of a specific card or library.
- Generation of behavioural forensic profiles for later comparison of the libraries including the closed, proprietary ones.
Tools for end-users
This section of the portal presents a set of carefully selected open-source tools and operating systems, forming a secure and usable desktop environment for the two defined user types – beginner and intermediate users. CyberSec4Europe evaluated multiple candidate open tools in each of the categories, and we provide specifications of ideal candidate traits and test evaluations for each individual tool category.