Set of tools allowing to verify that all devices (e.g., cryptographic smartcards cards) are matching the expected forensic profile to detect chips of different revision, malfunctioning, or even counterfeited one.
Currently, the user is dependent on the trusted distribution channel established with vendor. Basic chip identification like ATR or CPLC is insufficient as can easily be modified during the card personalization. SCRUTINY tool orchestrates a suite of other open tools analyzing target device and provide human-readable summary.
The typical procedure when applied to cryptographic smartcards is following:
- A card is inserted to reader, fingerprinted using suite of tools like JCAlgTest and compared with the expected profile.
- The device fingerprinting is based on the ATR, CPLC, supported algorithms, performance of selected crypto algorithms or power consumption traces for common cryptographic operations. The processing is configurable and may omit some of the analysis tool (e.g., power analysis which requires more elaborate measurement setup).
- The computed fingerprint is compared with expected one or optionally with the public database of results of already analyzed cards and html report with visualized similarities and differences is generated.
The forensic profile can be created either by the end-users or by (preferably) by the device vendor or evaluation facility and included as authorized certification artifacts later verifiable by end-users.
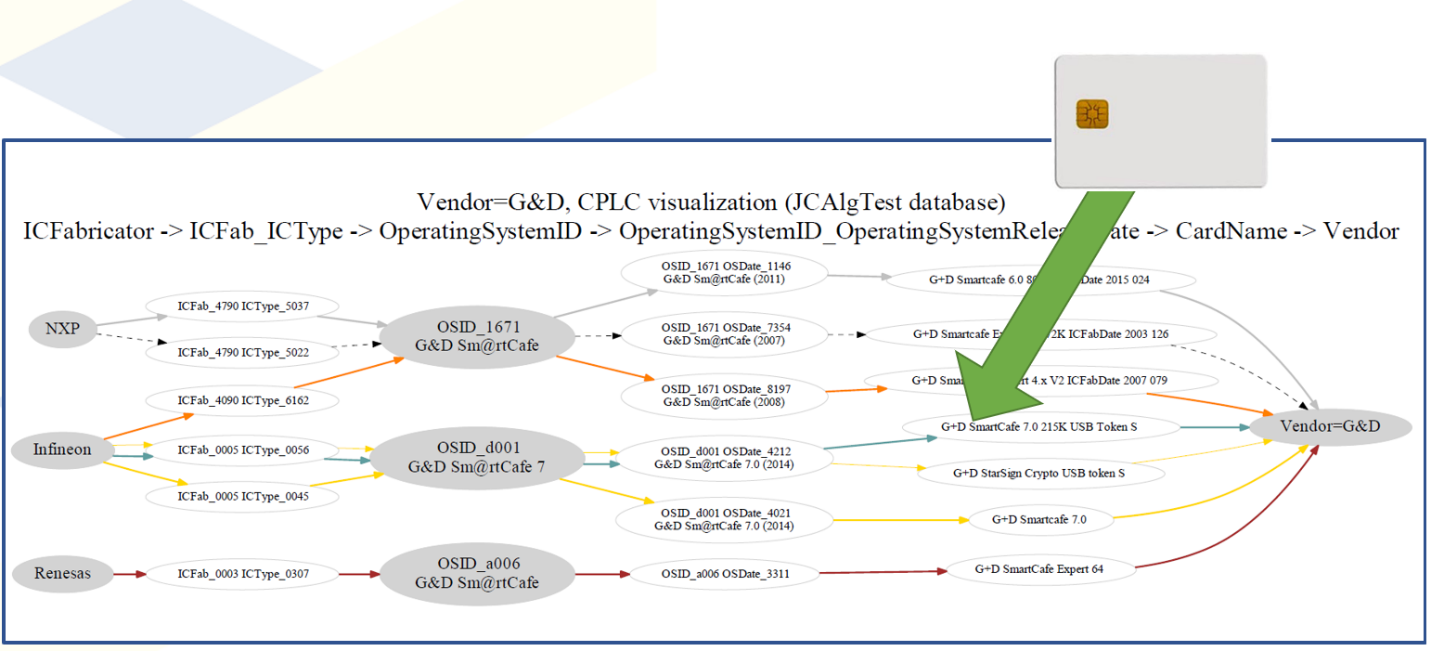
Figure 4 Example matching of target card fingerprint to database of known cards fingerprint (only CPLC matching is shown).
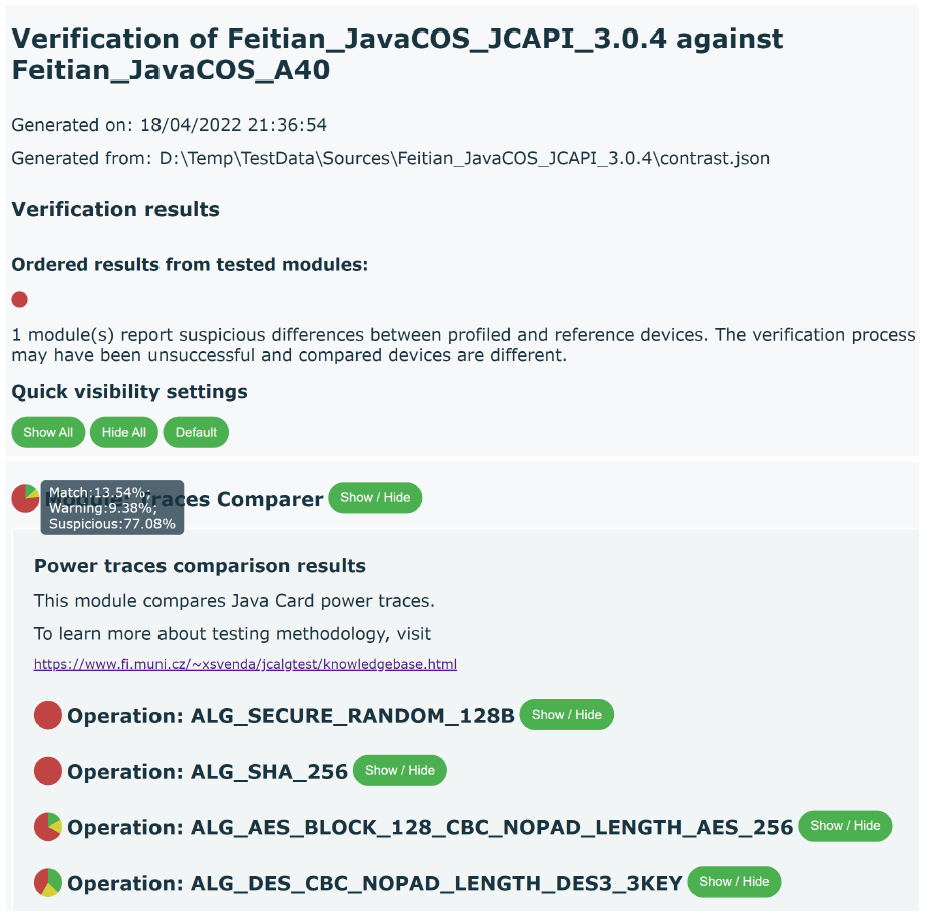
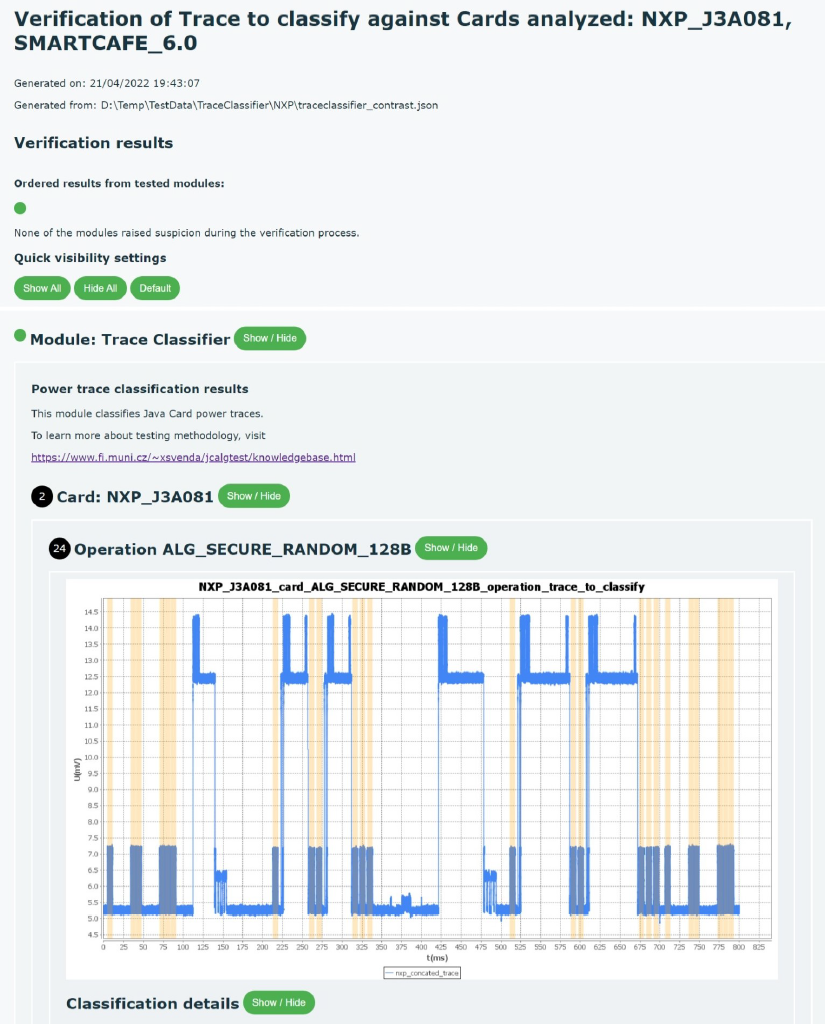
Figure 5 Example visualization of SCRUTINY summary report comparing two somewhat similar, but distinct types of smartcards.
For more detailed insights, please see the following:
[1] P. Svenda et. al., JCAlgTest – tool for JavaCards algorithm support testing, https://jcalgtest.org [2] I. Nagy, M. Podhorsky, P. Svenda, SCRUTINY git repository https://github.com/crocs-muni/scrutiny