The sec-certs set of tools download, process, and analyze security certificates issued under Common Criteria and NIST FIPS 140-2 schemes and turn these into computer-searchable and analyzable datasets. As a result, the following and other questions can be answered:
- What chips are impacted by flaw found in certified library X? Which certificates are relevant for my certified product Z? What products are affected by specific CVE vulnerability?
- Which devices were analyzed for timing side-channel leakage? Is ECC 521-bit curves supported?
- What are the trends of whole certification ecosystem regarding the archival rate, achieved security levels, usage of protection profiles and others?
The certification reports are the most detailed publicly available documents, yet currently available as pdf report in non-standardized format with only some metadata extracted (e.g., FIPS140-2 extracts referenced certificates). The sec-certs downloads source documents (pdf describing certified configuration and security target, csv and html with additional metada) and extract relevant information using regular expressions created for specific areas like certificate references, cryptographic algorithms, security assurance levels and many others. The information extracted is stored in open format (json) and futher used to analyze certificates, map them to other sources like CVE vulnerability database and construct aggregate visual presentation available at https://seccerts.org. The sec-certs tools also allows to process all data locally including additional own, non-public documents.
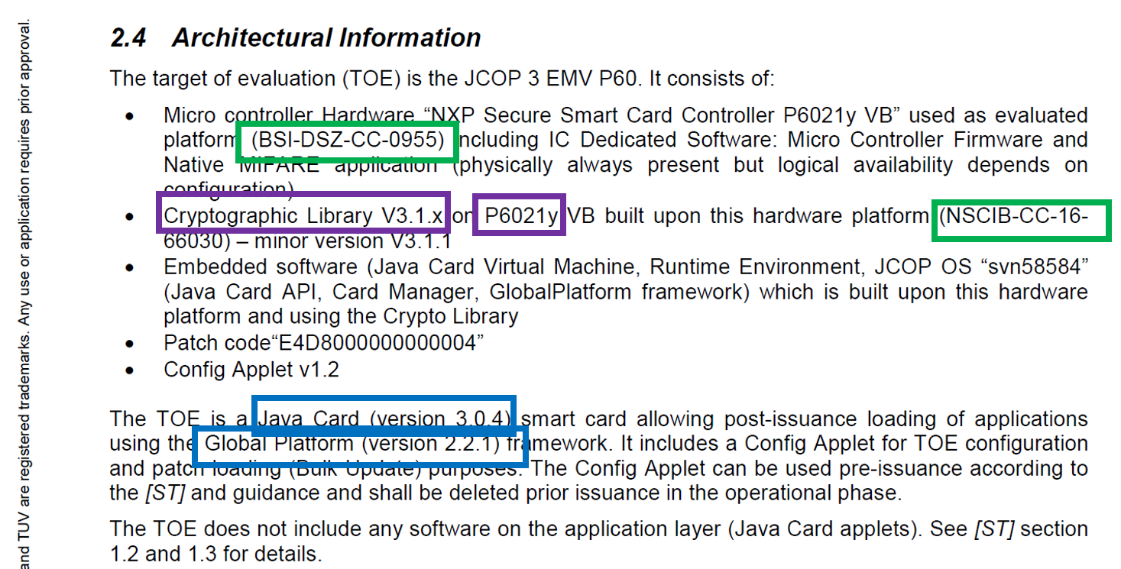
Figure 1 Example of interesting strings extractable via regular expressions, later stored in database (excerpt taken from NXP JCOP3 P60 CC certificate).
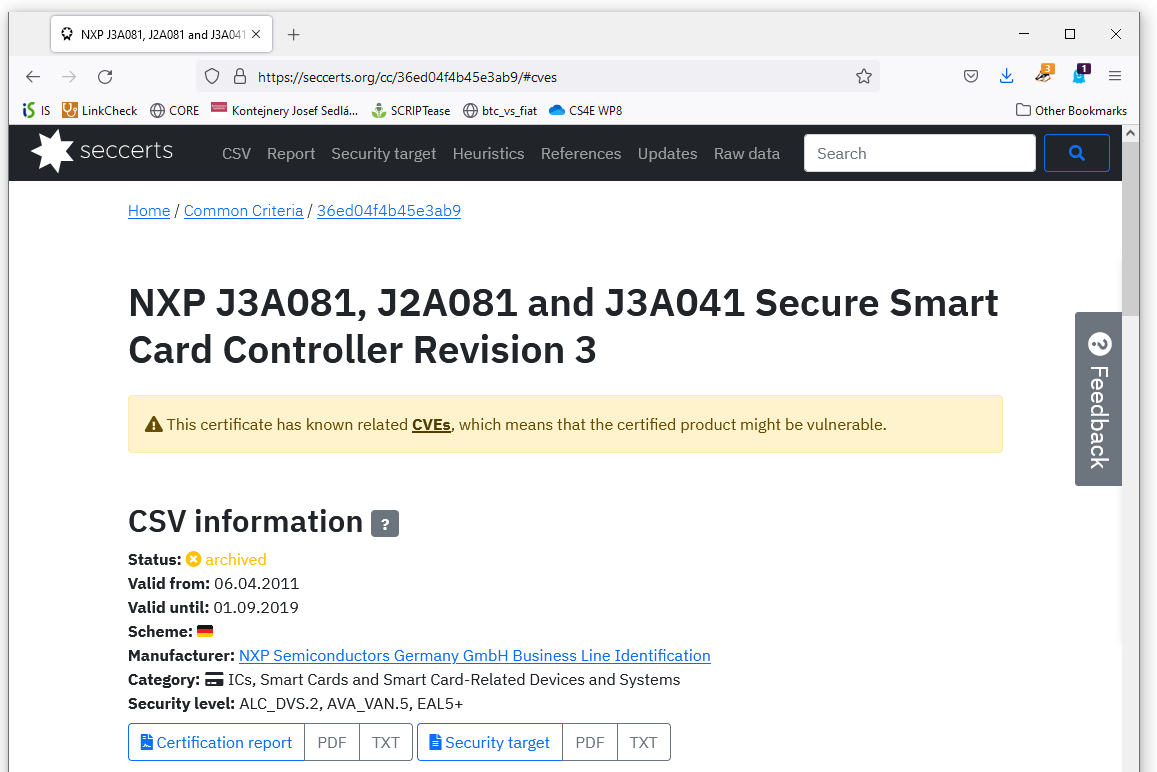
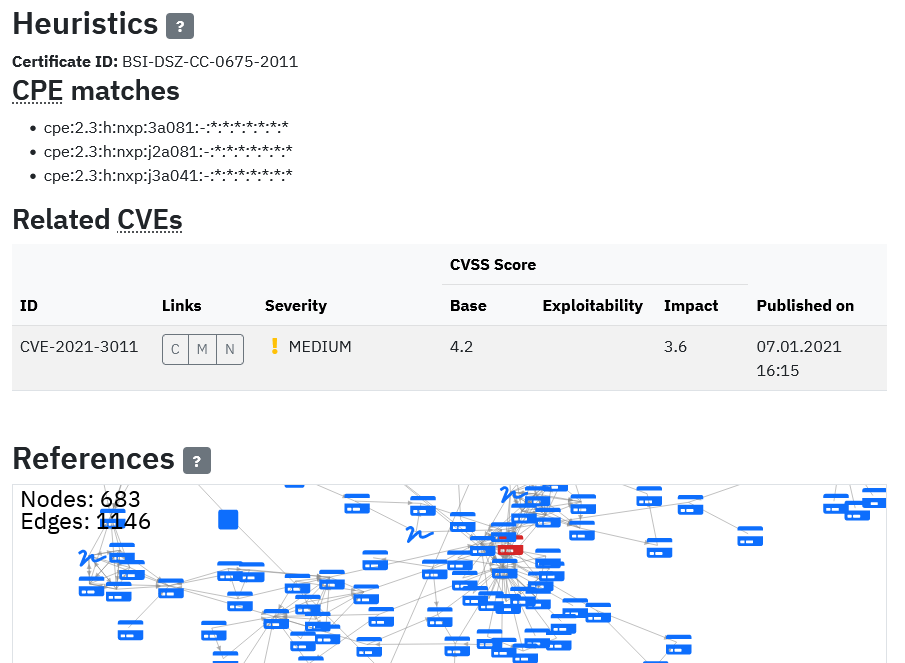
Figure 2 Example generated visualization for aggregated data extracted from CC certificate including matched CVE vulnerabilities and cross-certificate references graph.
For more detailed insights, please see the following:
[1] CRoCS MUNI, seccerts.org web portal, https://seccerts.org [2] CRoCS MUNI, sec-certs git repository https://github.com/crocs-muni/sec-certs/
