03 June 2021
Research Challenges on Incident Reporting in the Financial Sector
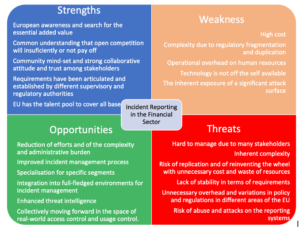
Several research challenges emerge from the need to report cyber and operational security incidents detected in financial institutions to different national and supranational Supervisory Authorities in order to be compliant with the increasing number of directives and regulations that affect the financial sector. In the second revision of the road mapping work carried out in CyberSec4Europe, an analysis of the strengths, weaknesses, opportunities and threats in this area, as well as an analysis of the impact that COVID-19 and the green dimension on incident reporting have helped to identify and address these research challenges.

Not only is the financial sector highly regulated but the current cyber incident reporting frameworks are also highly fragmented and create increasing complexity as well as additional regulatory and operational burdens for financial institutions with the need to report:
- to different authorities and supervisors,
- with different taxonomies, thresholds, timing, templates and information requirements; and
- at different local, national, European and industrial levels.
The three challenges
This situation is adding costs and unnecessary overhead in the management of incidents and can lead to different threats, such as diverting resources from where they are most needed after a cyber incident occurs limiting the impact of the incident and increasing the risks. Consequently, there are three distinct research challenges identified:
- To overcome the lack of harmonisation of procedures which arises from this need to comply with multiple regulations and supervisory authorities. Although there are some open source and commercial tools to support different tasks performed in the incident management process, off-the-shelf technology is not available yet which provides a clear opportunity to reduce the effort and complexity and improve the incident management and reporting procedures that need to be followed.
- To facilitate the collection and reporting of incident and/or data leaks which emerges during this process of gathering all the information required about a security incident and the preparation of reports in an easy and timely way.
- To promote a collaborative approach for sharing incident reports to increase risk quantification, mitigation, and overall cyber resilience. This challenge arises from the need for better cooperation among public and private entities to fight against cyber attacks and enhance cyber resilience, and to connect with the long-standing tradition of collaboration that the EU has established amongst the different stakeholders in the financial sector, the European awareness for the added value of this collaboration and the willingness that this collaboration and orchestration happen.
The following SWOT analysis characterises incident reporting in the financial sector:
The Impact of COVID-19
Although there are no indicators that the financial or banking sector has faced an increased number of cybersecurity incidents since the outbreak of COVID-19, there are some reports, as published by Interpol and Europol, confirming that, during the course of the pandemic, cyber criminals have made a major shift from targeting individuals and SMEs to attacking major corporations and critical infrastructures. In addition, the number of cybersecurity incidents as a result of the quick transition from on-premises to remote working has suffered a significant overall increase. A key finding from the Interpol report is that malicious domains registrations increased by 569 per cent in the month from February to March 2020. Europol emphasises that not reporting cases to law enforcement agencies will obviously hamper any efforts, as important evidence and intelligence from different cases can be missed. Europol also reports that in the European Money Mule Action (EMMA 6) operation, only a few COVID-19 related cases were reported.
Embracing the green dimension
The European Green Deal, an ambitious plan put forward by the European Commission to green the European economy, has also had an impact on incident reporting solutions. Current incident reporting processes involve generating reports, which almost always are printed on paper. Printed reports could be replaced by an environment-friendly digital platform for mandatory incident reporting which would reduce the need for wood and the pollution emissions associated with paper manufacturing. Such a digital solution would not only reduce pollution, but also provide additional functionality such as aggregation and data visualisation as related to cybersecurity incidents.
How CyberSec4Europe is addressing the challenges
To overcome those research challenges identified, the following activities are being carried out by CyberSec4Europe:
- Definition and development of:
- a mandatory incident reporting workflow for the financial sector
- a data model for collecting the information required for the mandatory incident reporting in the financial sector
- a common severity event classification procedure in the financial sector
- Design and deployment of a prototype of incident reporting platform, integrating open source tools (such as TheHive and Cortex) with assets implemented in the project to cover the different stages in the incident reporting process. The platform will be also connected with threat intelligence data sharing platforms through MISP.
- Implementation of tools for:
- workflow enforcement and reporting. The Atos Incident Reporting Engine (AIRE) has been integrated with the open source incident management and response tool TheHive for the enforcement of the financial incident reporting workflow, support for managerial judgement and the preparation of the reports that need to be sent for mandatory incident reporting according to different regulations.
- threat intelligence data sharing. The three assets integrated in the platform to improve trustworthiness and reliability for threat intelligence data sharing using MISP and the qualification of indicators of compromise to improve actionability are:
- Trustworthy APIs for enhanced threat intelligence sharing (TATIS),
- Reliable Cyber-Threat intelligence sharing (Reliable-CTIs) and
- Threat Intelligence integrator (TIE)
Further reading on the latest incident reporting and CyberSec4Europe’s other roadmapping activities can be found in the deliverable report, Research and Development Roadmap 2
Susana González Zarzosa, Atos Spain
Vanesa Gil Laredo, BBVA Group
Laura Colombini, Intesa Sanpaolo SpA
Jani Päijänen, Jyväskylä University of Applied Sciences (JAMK)
Wouter Joosen, KU Leuven
Ivan Pashchenko, University of Trento
