One of the main goals of this task was to identify research challenges, requirements and approaches in all stages of the lifecycle of software.
Research Challenges in Secure Software Lifecycle
One of the main outcomes was the following set of research challenges related to security and privacy issues in the lifecycle of software:
- Assessing security and privacy through the life cycle
- Assessing privacy properties of complex systems
- Privacy protection and user empowerment in IoT
- Securing unsafe and legacy software
- Protecting leaked credentials
- Secure Access control in heterogeneous systems
- Manageable and understandable security engineering
- Unreliable risk estimates short-term research
- Automated and verified network security configuration in highly dynamic environments
- Scalable and private industrial blockchain
- Scaling TEEs for cloud applications
(All were considered short-term research except for challenge 9). The challenges are described in detail in the document D3.9 Research challenges and requirements for secure software development.
Smart City Demonstrator
The analysis of the research challenges led to the identification of promising tool-supported approaches to be developed in order to address the challenges. A total of 13 tools to support different activities in the lifecycle of software was developed and demonstrated on a common smart-cities scenario as illustrated in the figure below.
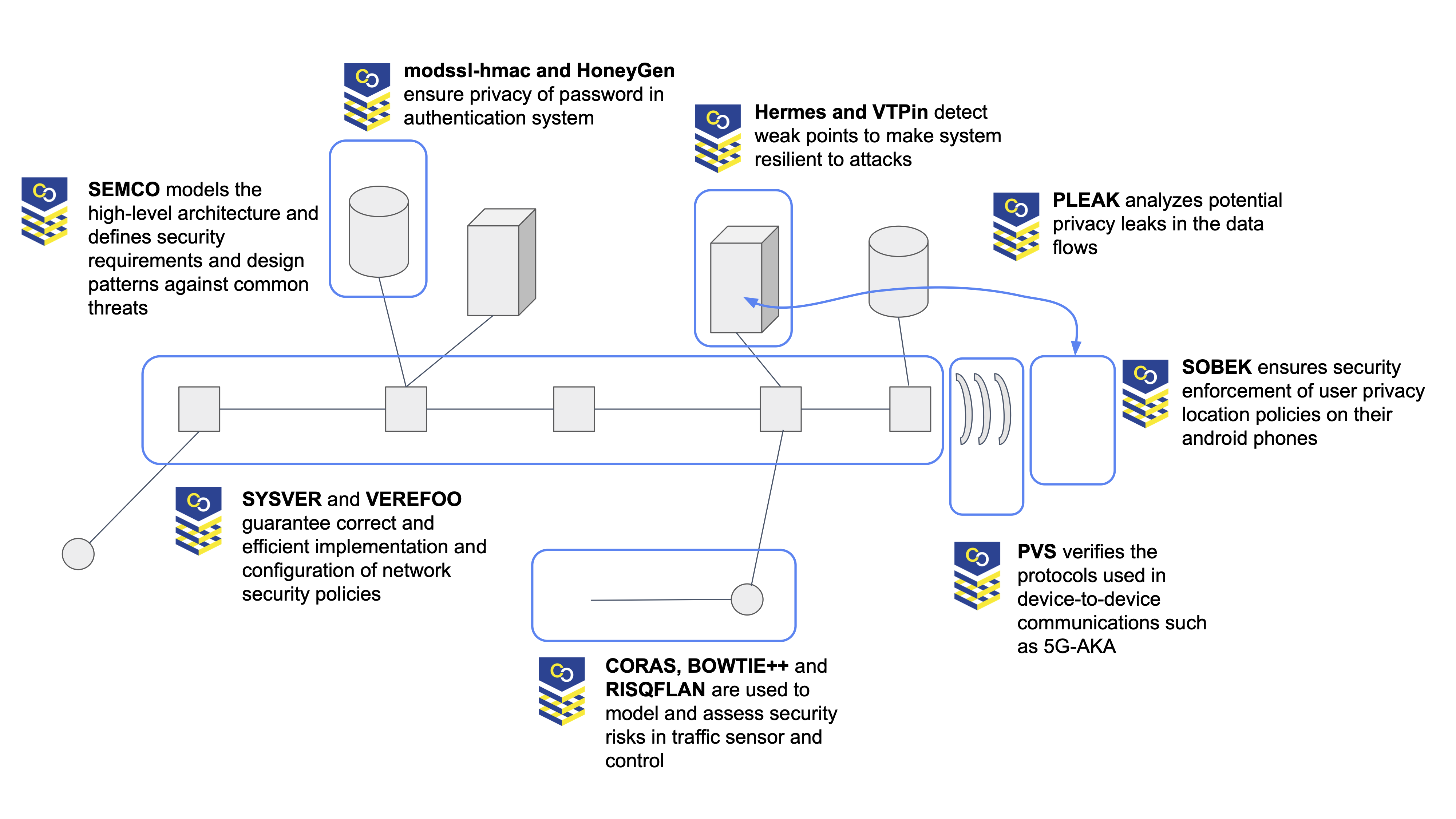 The demonstrator is based on a common scenario of a smart city platform featuring some of the security challenges typical from such platforms (as identified in the smart city demonstrators). The following assets are part of the demonstrator: CORAS, BOWTIE++, Hermes, SOBEK, VEREFOO, SYSVER, SEMCO, PLEAK, and PVS. The demonstrator follows the global architecture described above, with each asset covering a specific building-block of the architecture as follows:
The demonstrator is based on a common scenario of a smart city platform featuring some of the security challenges typical from such platforms (as identified in the smart city demonstrators). The following assets are part of the demonstrator: CORAS, BOWTIE++, Hermes, SOBEK, VEREFOO, SYSVER, SEMCO, PLEAK, and PVS. The demonstrator follows the global architecture described above, with each asset covering a specific building-block of the architecture as follows:
- SEMCO models the high-level architecture and define security requirements and design patterns against common threats.
- Modssl-hmac and HoneyGen ensures the privacy of passwords in the authentication system.
- Hermes and VTPin detects weak points to make the system resilient to attacks.
- PLEAK analyses potential privacy leaks in the data flows.
- SOBEK ensures security enforcement of user privacy location policies on their android phones.
- PVS verifies the protocols used in device-to-device communications such as 5GAKA.
- CORAS, BOWTIE++ and RISQFLAN model and assess security risks in traffic sensors and control.
- SYSVER and VEREFOO guarantee correct and efficient implementation and configuration of network security policies.
The main demonstrator of the Software Development Lifecycle task is reported in D3.15 – Proactive Approaches to Secure Software Development.
For further information the corresponding GitHub entry has details of online proof-of-concept demonstrators and repositories, videos and a listing of dissemination in scientific journals and articles.
SEMCO
Modssl-hmac
HoneyGen
PLEAK
SOBEK
PVS
CORAS
BOWTIE++
RISQFLAN
SYSVER
VEREFOO
